Metasploit is a widely used open-source framework designed for penetration testing, vulnerability assessment, and exploit development in the field of cybersecurity. Developed originally by H.D. Moore in 2003 and later acquired by Rapid7 in 2009, Metasploit has become a pivotal tool for both security professionals and, unfortunately, cybercriminals.
Core Features and Purpose
• Penetration Testing: Metasploit allows security engineers and ethical hackers to simulate real-world cyberattacks on networks, servers, and applications. This helps organizations identify and remediate vulnerabilities before they can be exploited by malicious actors.
• Exploit Development: The framework provides a platform for developing, testing, and executing exploit code against remote targets. It houses a vast database of exploits—over 2,300, covering a wide range of platforms and vulnerabilities.
• Modular Design: Metasploit’s modular architecture lets users mix and match exploits (code that leverages a vulnerability), payloads (code executed after exploitation, such as a remote shell), and auxiliary modules (tools for scanning, sniffing, etc.) to customize attacks or tests.
How Metasploit Works
The typical workflow involves:
1. Information Gathering: Integrating with tools like Nmap or Nessus to scan and identify vulnerabilities on target systems.
2. Selecting Exploits and Payloads: Choosing an appropriate exploit for the identified vulnerability and pairing it with a payload (e.g., Meterpreter, a powerful interactive shell).
3. Launching the Attack: Configuring and executing the exploit, which, if successful, delivers the payload to the target system.
4. Post-Exploitation: Once access is gained, Metasploit offers tools for privilege escalation, data collection, and persistence.
Quick commands
Export
db_export -f xml FILENAME.xml
Import
db_import FILENAME.xml
Write hosts
spool hosts.txt
hosts
Write services
spool services.txt
services
Searching in Metasploit
- Search for:
sharepoint rce
Display only remote code execution exploits for Microsoft SharePoint. - Search for:
cve-2020
Display only exploits with assigned CVE from year 2020. - Search for
eternalblue
Display only modules for exploiting the MS17-010 SMB vulnerability. - Search for
privilege escalation
Display only Windows privilege escalation exploits. - Search for:
bypassuac
Display only bypass UAC exploits. - Search for:
proxylogon
Display only modules exploiting vulnerabilities against Microsoft Exchange Server.
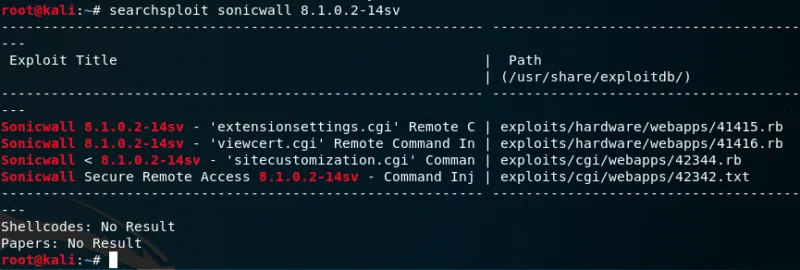
Adding exploit from searchsploit
Look for the exploit you want to add:
searchsploit sonicwall 8.1.0.2-14sv Make a note of the path for the exploit.
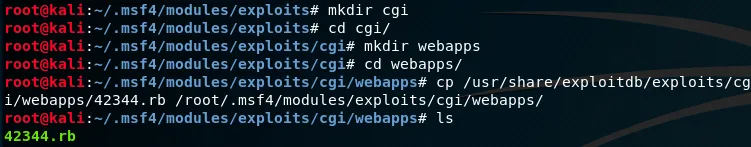
Next, you would need to create a folder in the .msf4/modules directory that correlates with the path in exploit-db. So in this case I will add exploits/cgi/webapps. You’ll probably need to create the exploits directory under /root/.msf4/modules first.
Go to your newly created folder and copy the exploit:
cp /usr/share/exploitdb/exploits/cgi/webapps/42344.rb /root/.msf4/modules/exploits/cgi/webapps/Make sure that you specify both, the root path (its specified right underneath the title “Path” in the searchsploit search output) and the relative path.
Once you are done run updatedb
If your msfconsole is running make sure to close it and reopen again after running updated.
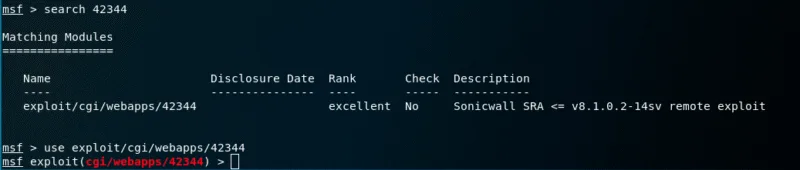
You can now use the exploit.You will also see that the number of exploits is increased by one.