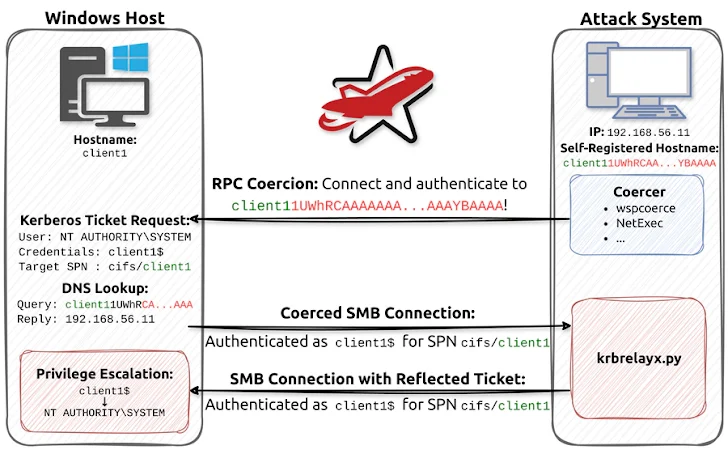
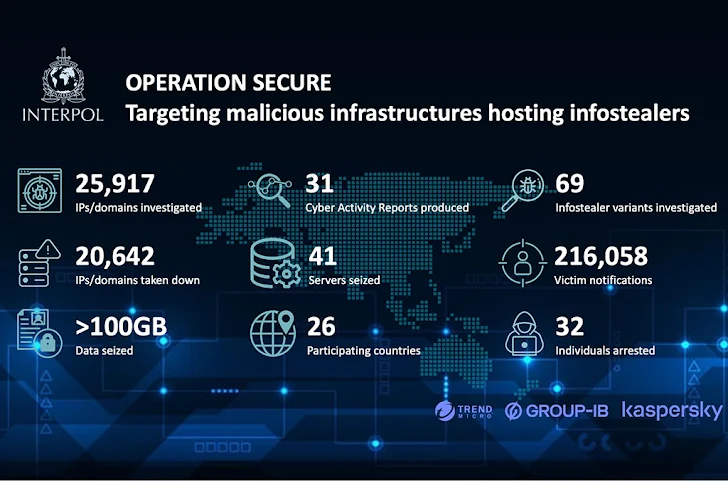
Posted inCybersecurity News
Bitsight’s Warning: 40,000 Security Cameras Exposed Globally
Bitsight, a cybersecurity ratings company, has issued a stark warning after its TRACE research team discovered over 40,000 internet-connected security cameras streaming live footage openly on the internet, with no passwords or meaningful security protections in place. These cameras, intended for use in homes, businesses, factories, hospitals, and even public transportation, are inadvertently providing public access to sensitive locations and information.