Posted inCybersecurity News
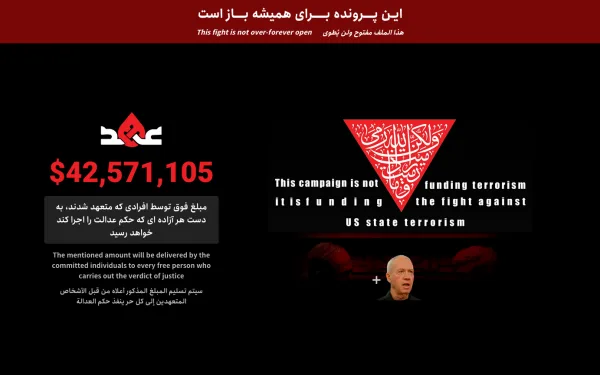
Record-breaking 7.3 Tbps distributed denial-of-service (DDoS) attack sets a new benchmark for the scale and intensity of hyper-volumetric attacks.
In a concerning escalation of cyber threat activity, a record-breaking distributed denial-of-service (DDoS) attack peaking at 7.3 terabits per second (Tbps) was recently mitigated, setting a new benchmark for the scale and intensity of hyper-volumetric attacks. This unprecedented surge, observed and neutralized by global cybersecurity firm Cloudflare, underscores the rapidly evolving threat landscape facing global infrastructure providers, telecommunications networks, and digital platforms.