Posted inCybersecurity News
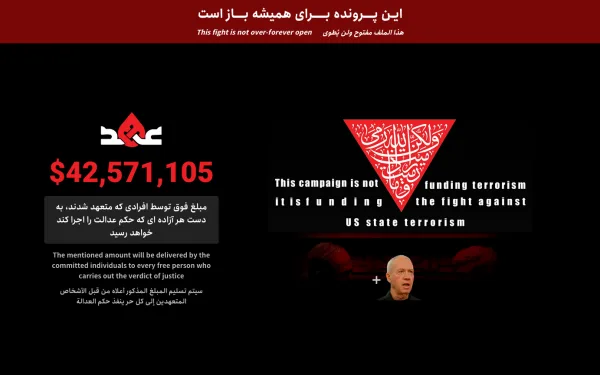
Belk confirms unauthorized access and theft of 156 gigabytes of sensitive company data.
Belk, the North Carolina-based department store chain with nearly 300 locations across the southeastern United States, has confirmed that it was the victim of a cybersecurity breach in May 2025. The cyberattack, attributed to the ransomware group DragonForce, resulted in the unauthorized access and theft of 156 gigabytes of sensitive company data.